[VulnHub] - Jarbas: 1 Walkthrough
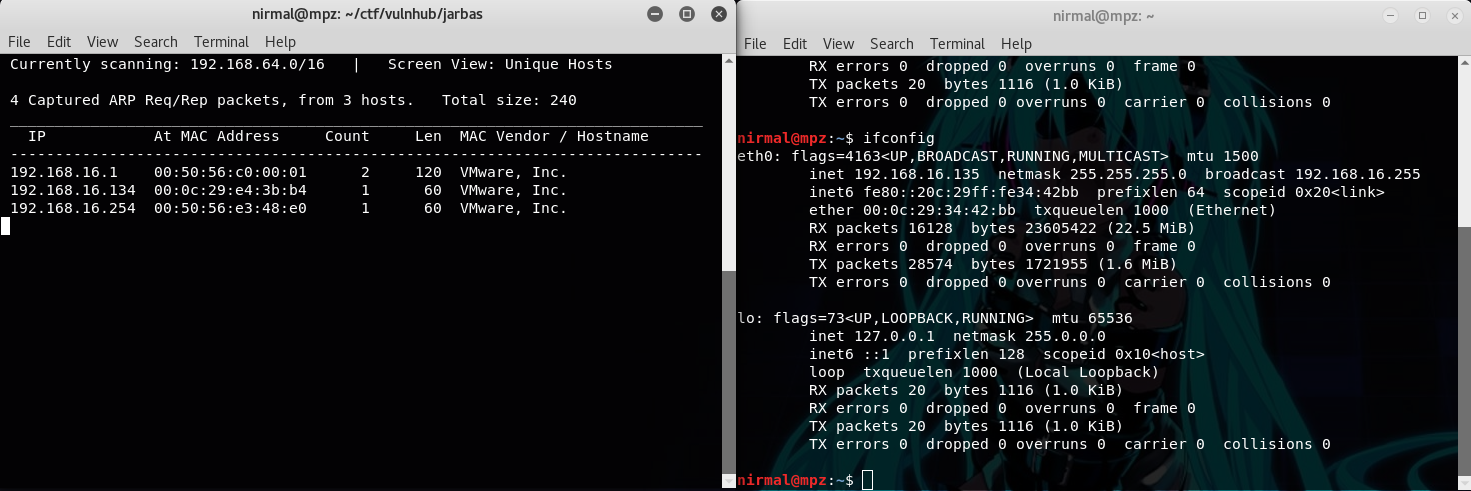
~ Spoiler Alert ~ Recently I did Jarbas from Vulnhub and below is my walkthrough for this machine. Firstly, to obtain the IP address of the target machine, I used netdiscover. My kali machine booted later than the target machine, so obviously Jarbas machine's IP is 192.168.16.134 A quick port scan on the IP address revealed some open ports like 22 (SSH), 80 & 8080 (HTTP), 3306 (mysql). No SSH creds were initially provided and mysql also didn't allow to access remotely so I skipped port 22 and 3306 and moved towards the port 80. Homepage for port 80 looks something like below. In the machine's description, the author has mentioned that this machine (Jarbas) is a tribute to a Brazilian Search engine of the 90's. The homepage of the machine also displays a static page copied from wayback machine of the same search engine jarbas.com.br. Since it's a static page directly copied from wayback machine, there's nothing interesting so I moved to port 80...
